Content Security Protocol (CSP) support
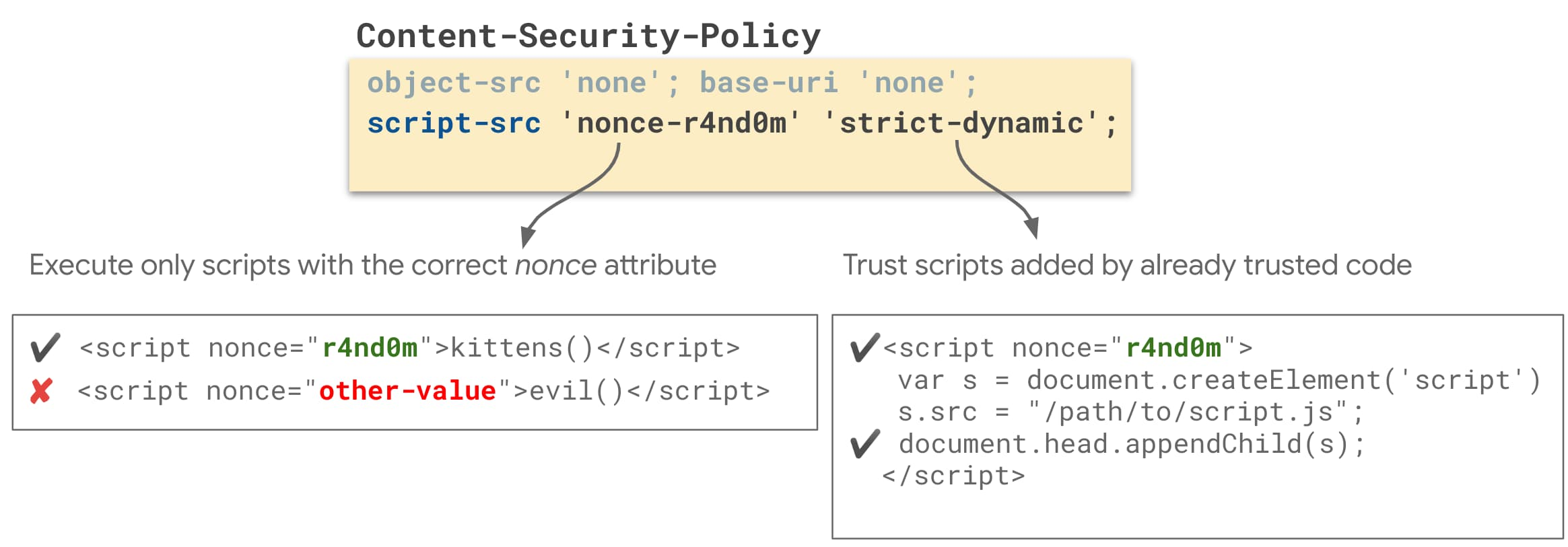
Modern websites increasingly adopt strict Content Security Policies. In particular, configurations based on nonce, where dynamically executed scripts are allowed only when they carry a valid nonce attribute.
Clickio Consent has been updated to work seamlessly under Strict CSP with nonces, without requiring unsafe-inline in script-src.
Our solution works with a fully strict, nonce-based policy such as:
Content-Security-Policy:
script-src 'nonce-{RANDOM}' 'strict-dynamic';
object-src 'none';
base-uri 'none';How to integrate Clickio Consent with Nonce-Based Strict CSP
To enable full compatibility, simply add a unique nonce="<value>" attribute to:
1. The Clickio Consent script tag
<!-- Clickio Consent Main tag -->
<script async src="//clickiocmp.com/t/consent_{Clickio Site ID}.js" nonce="{RANDOM}"></script>2. Any default Consent Mode configuration script (if used)
<!-- Default Consent Mode config -->
<script nonce="{RANDOM}">
//<![CDATA[
// Your Consent Mode default config here
//]]>
</script>